Wipr 2 GitHub impersonation
The other day, I googled "wipr github" to see if there was an open-source GitHub repository for the popular macOS app Wipr 2. Instead, I saw a search result for a phishing page hosted on GitHub.
The phishing page belongs to the Wipr-2-Download-App GitHub organization (defanged below):
hxxps[://]github[.]com/Wipr-2-Download-App
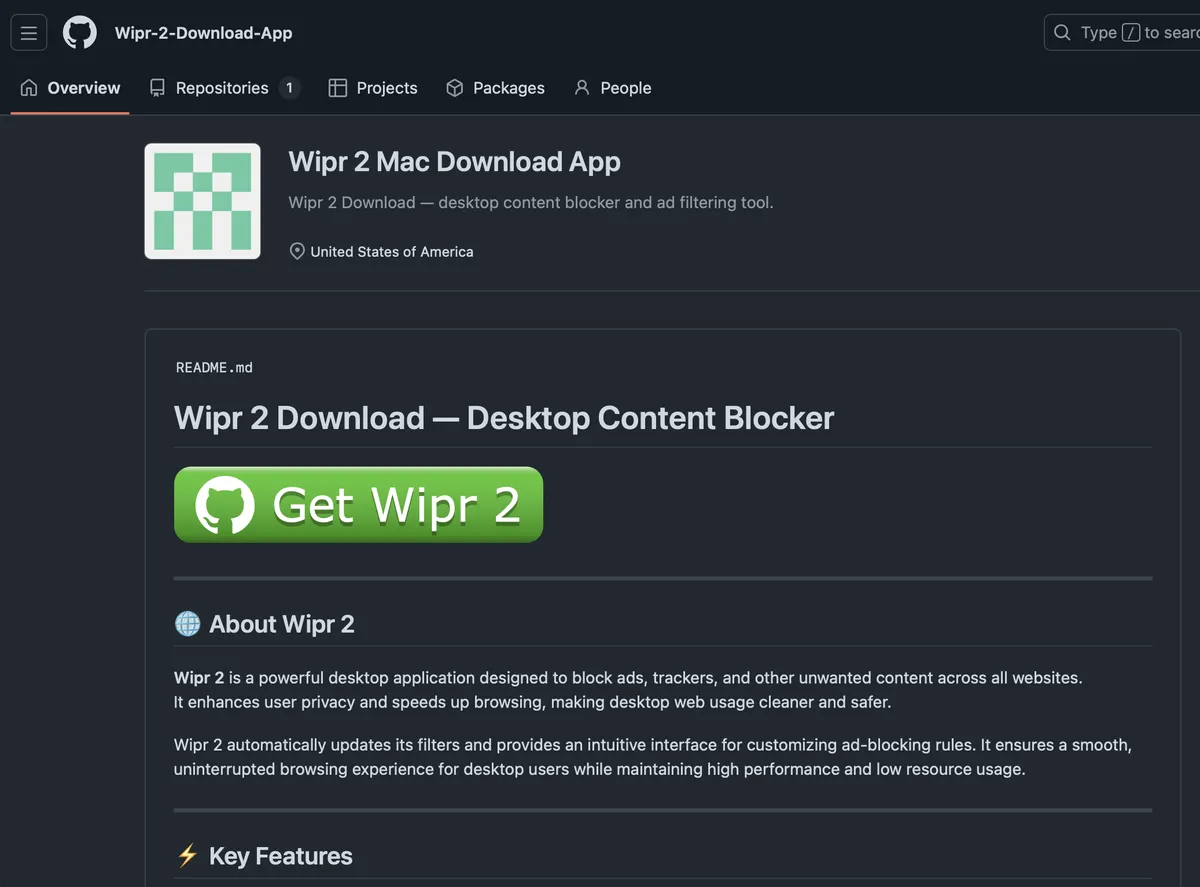
The Wipr-2-Download-App organization has one public repository, named .github. That repo contains a file named profile/README.md, which GitHub renders as HTML on the organization's Overview tab.
The repo has one branch, named main, with three commits (defanged below):
commit 8f297958a99e31ab461b9e7dd07d1e7d7ac08b30 (HEAD -> main, origin/main, origin/HEAD)
Author: lanateneteuphoria <keikomaria7192@outlook[.]com>
Date: Mon Oct 20 10:20:02 2025 -0600
Update README[.]md
commit 7edf2fcea1db53fdec4277d6f7c9c85c432545f3
Author: lanateneteuphoria <keikomaria7192@outlook[.]com>
Date: Sun Oct 12 12:47:07 2025 -0400
Create README[.]md
commit aa14582cd7d90c5bbc267ca34a11d44d1064b279
Author: lanateneteuphoria <keikomaria7192@outlook[.]com>
Date: Sun Oct 12 12:45:19 2025 -0400
Initial commit
The lanateneteuphoria user also exists on GitHub. Their GitHub user page reads "Joined GitHub on September 28, 2025". They have no other public activity besides these three commits.
Unfortunately, the GitHub API does not list any SSH public keys or GPG public keys for the lanateneteuphoria user. (The public API endpoints for this are https://api.github.com/users/USER/keys and https://api.github.com/users/USER/gpg_keys respectively.)
Anyway, the big, green "Get Wipr 2" download button leads to a github.io link (defanged below):
hxxps[://]dowloader-desktop-app[.]github[.]io/[.]github/?offer=Wipr%202
Given how github.io URLs work, the subdomain dowloader-desktop-app corresponds to the GitHub organization dowloader-desktop-app.
The dowloader-desktop-app GitHub organization has one public repo, also called .github. The repo has one branch, main , with three commits (defanged below):
commit f3a31a9277457cda734a4a13f301d36e47d12ca8 (HEAD -> main, origin/main, origin/HEAD)
Author: kamikadzebro84-collab <elianamine7093@hotmail[.]com>
Date: Mon Oct 20 07:44:27 2025 -0600
Update index[.]html
commit a054499a1a65ef4be53e7a40f1d089113ea4cddc
Author: kamikadzebro84-collab <elianamine7093@hotmail[.]com>
Date: Sat Oct 18 14:35:56 2025 -0700
Add files via upload
commit 1203d96e3370e01a327e3d1b3b9a5c0ad3171c69
Author: kamikadzebro84-collab <elianamine7093@hotmail[.]com>
Date: Sat Oct 18 14:34:07 2025 -0700
Initial commit
The kamikadzebro84-collab GitHub user exists and joined GitHub on October 1, 2025. The GitHub API returns no SSH public keys or GPG public keys. They have no other public activity besides these three commits.
Anyway, this second .github repo contains an index.html file that corresponds to the github.io phishing page. I archived the index.html file for future reference.
- archive.today (unmodified): https://archive.ph/akQBt
- Internet Archive (some content is unfortunately rewritten to include additional
https://web.archive.orglinks): https://web.archive.org/web/20251025061137/https://raw.githubusercontent.com/Dowloader-Desktop-App/.github/main/index.html
The index.html file contains some anti-analysis measures, like a redirect delay.
const REDIRECT_DELAY_MS = 200;
The delay interferes with services like urlscan.io, which fails to perform the subsequent redirect:
https://urlscan.io/result/019a198c-94b2-713b-93d4-7304002c07ed/#summary
The index.html file also contains Russian-language comments, like:
// Куда вести по ОС (замени на свои домены, без завершающего /)
A rough machine translation is:
// OS URL (replace with your domains, without the trailing /)
Perhaps this indicates that the site is based on another author's phishing kit.
The index.html file also contains an APP_URL string (defanged below).
const APP_URL = "hxxps[://]script[.]google[.]com/macros/s/AKfycbwip_VgPEumBXeWuX_OEX6huIMHfPXidiweHpHR-fGUQIqpcR-mAMAHC1JCUQyJne3n0Q/exec";
The APP_URL string is used only once in the logRedirect function:
// non-blocking лог через <img>
function logRedirect({os, offer, targetUrl, ip, country, countryCode}){
A rough machine translation of the comment is "non-blocking log through img", which makes me think that APP_URL is used for tracking purposes.
Of primary interest, the index.html file also contains this DEST dictionary (defanged below):
const DEST = {
windows: "hxxps[://]pwin[.]onelink[.]me/zmFc/dt38769z",
macos: "hxxps[://]pmacos[.]onelink[.]me/m5yY/q5vbjgvh",
ios: "hxxps[://]github[.]com/pricing",
android: "hxxps[://]github[.]com/pricing",
linux: "hxxps[://]github[.]com/pricing",
other: "hxxps[://]github[.]com/pricing"
};
This appears to help redirect Windows and macOS devices to a following phishing stage, while ignoring other device types.
Here are urlscan.io results for the next Windows and macOS phishing stages:
- Windows: https://urlscan.io/result/019a19cc-2354-769b-912b-e6b50e616412/
- macOS: https://urlscan.io/result/019a19cc-f8c8-73f2-9178-b6277e3ede6a/
The macOS link leads to a 404 Not Found page on cotlesgengeral[.]com, which is a dead end.
The Windows link leads to a page with a "Download Your File" button on ourhealingpoweriswithin[.]com.
On that page, a script.js script executes code when the download button is clicked. It appears that the URL to the actual download is generated at runtime:
const url = `archiveProxy.php?domain=${domain}&version=${randomVersion}&id=${id}`;
So, let's try to find valid values for each of the three variables.
First, domain can be "unknown".
const domain = document.referrer
? new URL(document.referrer).hostname
: "unknown";
Second, randomVersion can be "_6.3.2".
randomVersion = `_${Math.floor(Math.random() * 10)}.${Math.floor(
Math.random() * 10
)}.${Math.floor(Math.random() * 10)}`
Third, id must be 3, per this line in the DOM:
startFileCreationAndDownload(3);
So, we can build this valid URL (defanged below):
hxxps[://]ourhealingpoweriswithin[.]com/archiveProxy[.]php?domain=unknown&version=_6[.]3[.]2&id=3
This works! The downloaded file is named launcher_6.3.2.zip and has SHA-256 hash ea34311817c42bc60308afae9fd354fb68e637317de9549302d2afc3ec744506.
VirusTotal gives it a 30/67 risk score and identifies it as a Windows trojan in the tedy or ylaud families:
https://www.virustotal.com/gui/file/ea34311817c42bc60308afae9fd354fb68e637317de9549302d2afc3ec744506
VirusTotal also finds that the trojan makes network connections to a Rhadamanthys C2.
Some time after obtaining the payload, I tried to find other, similar malicious GitHub organizations. Unfortunately, neither GitHub code search, grep.app, nor Google search were that useful. I wish GitHub would improve their code search to make threat hunting a bit easier.
IOCs
| type | value |
|---|---|
| URL | hxxps[://]github[.]com/Wipr-2-Download-App |
| URL | hxxps[://]github[.]com/dowloader-desktop-app |
| URL | hxxps[://]pmacos[.]onelink[.]me/m5yY/q5vbjgvh |
| URL | hxxps[://]pwin[.]onelink[.]me/zmFc/dt38769z |
| Domain | cotlesgengeral[.]com |
| Domain | dowloader-desktop-app[.]github[.]io |
| Domain | ourhealingpoweriswithin[.]com |
| MD5 | 850fbac876aff18ebf2405e951aa7bd4 |
| SHA1 | 73c389405fa6835cbe0d6b0bf9209352fa909b81 |
| SHA256 | ea34311817c42bc60308afae9fd354fb68e637317de9549302d2afc3ec744506 |
keikomaria7192@outlook[.]com |
|
elianamine7093@hotmail[.]com |